
Problems & Demands
-
 System is too complicated to manage
System is too complicated to manage
-
 Information Resource has ‘no boundary’
Information Resource has ‘no boundary’
-
 Urgent to innovate technical applications
Urgent to innovate technical applications
-
 Urgent to improve the security concepts
Urgent to improve the security concepts
Technical Solutions
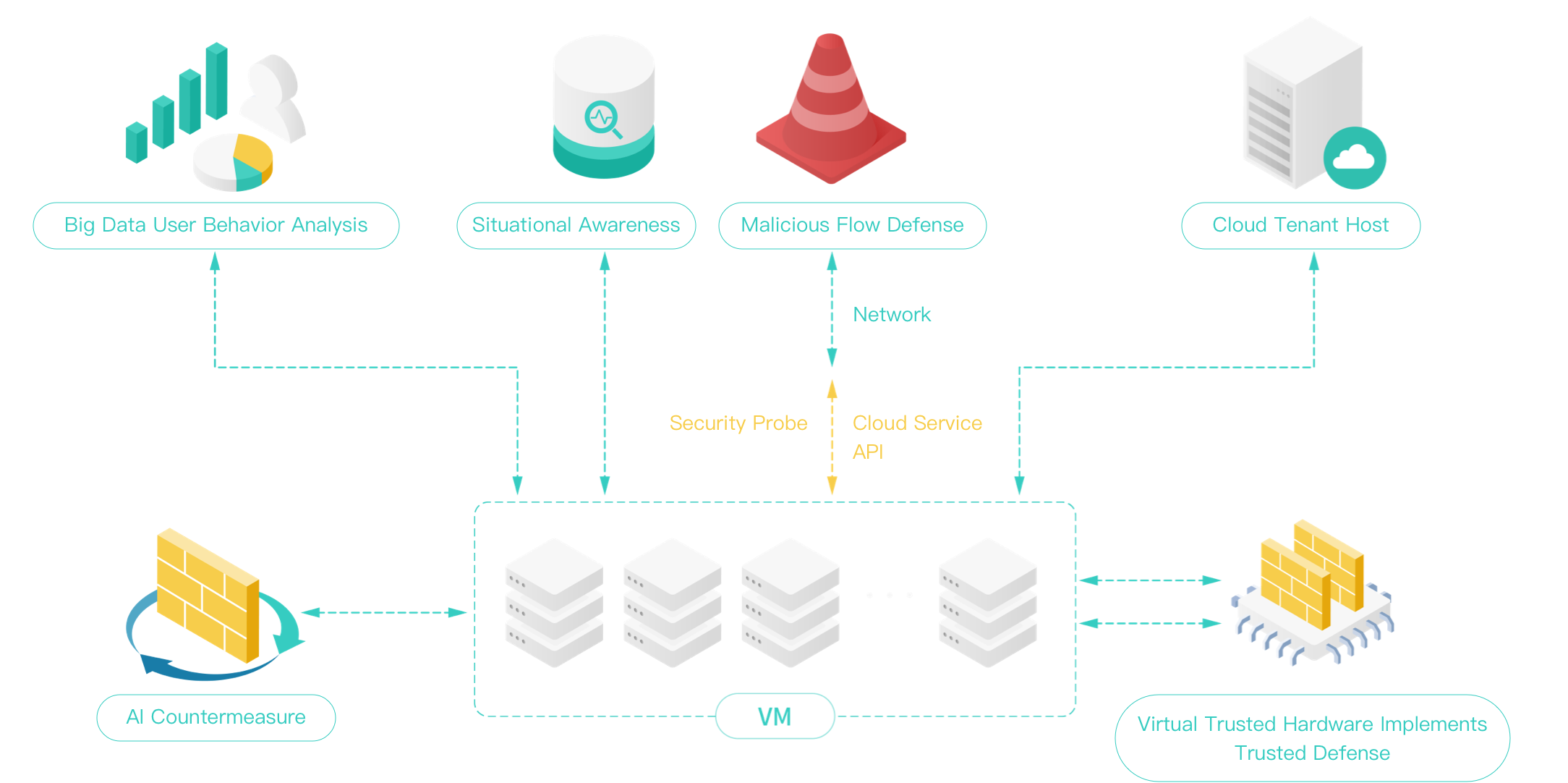
01.
Defense Capabilities
Introduces new architecture mechanism and AI technology, improves the security capability of virtual host on cloud improved and the ability to resist unknown attack.
02.
Management capabilities
Strengthens the security management of business systems on the cloud, especially the fine management of security mechanism based on different users (devices)
03.
Service Capabilities
Through the establishment of cloud security management and service platform, the following can be achieved:
- Improves the security of business systems on the cloud
- Integrates new security technologies quickly
- Provides the friendly visual interface management
- Reduces the complexity of system security operation and maintenance management
Safety Protection
Effectively improves the security of the cloud business system, to provide multi-level security protection for the cloud computing platform and the business systems it carries, such as data security, application security and system security.
Autonomous Countermeasure
Combined with threat intelligence and AI anticipates, makes countermeasures, and assists on operations and maintenance, handling things effectively.
UEBA
Generates user portraits and perceives abnormal behaviors by making big data analysis according to the log contents and combining user permissions and operation behaviors.
Problems & Demands
-
 Business Continuity
Business Continuity
-
 Data Security
Data Security
-
 Unknown Threat
Unknown Threat
-
 Development, operation & maintenance efficiency
Development, operation & maintenance efficiency
Technical Solutions
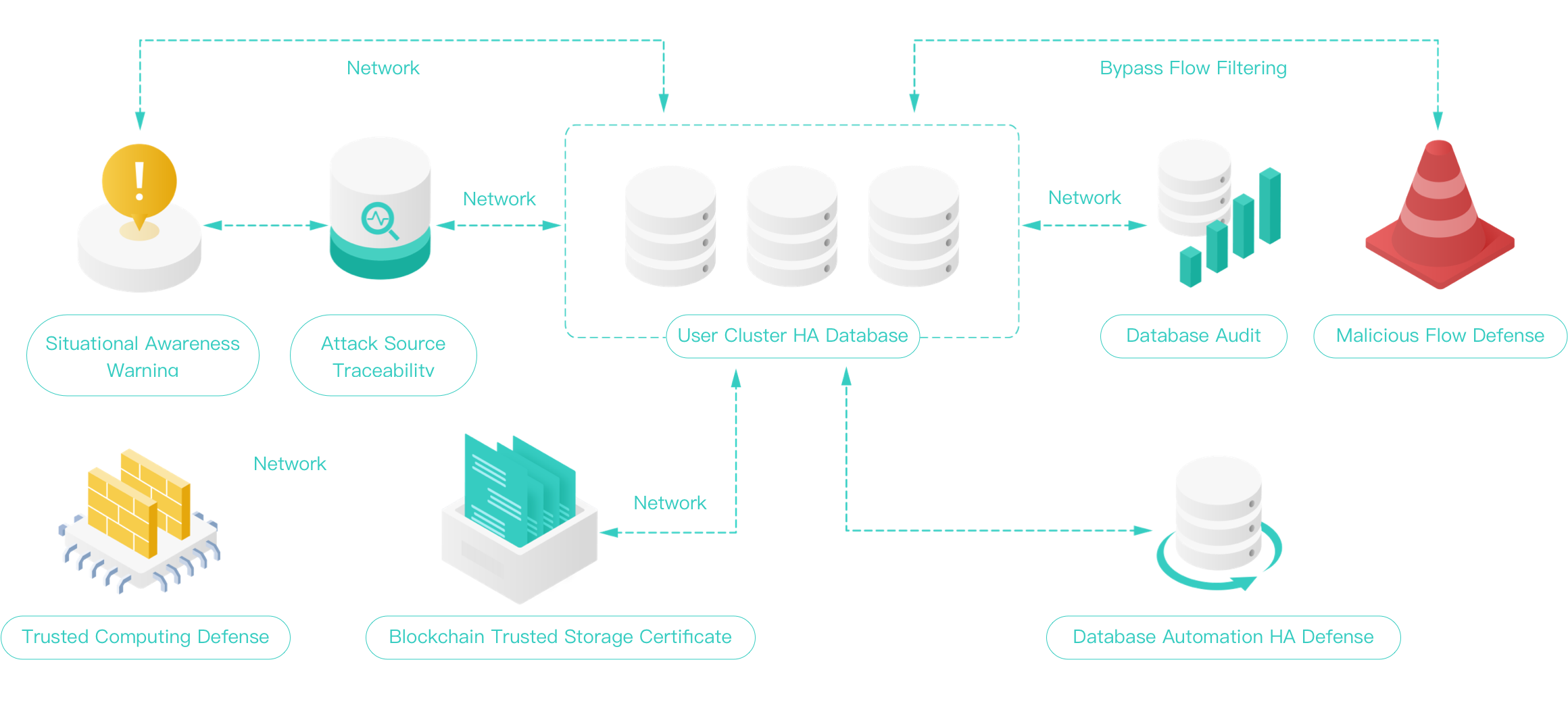
01.
Tamper-Proofing
Builds a secure tamper-proof and traceability system for key log information, based on the technical characteristics of block chain technology, such as distributed, open, and transparent, non-tamper, and high security.
02.
Traceability
Realizes the efficient synchronization of data from multiple data sources and nodes, the collection and centralized audit of important data, and then to realize the blockchain storage and traceability scheme of financial key information system infrastructure.
03.
Powerful Management
Effectively improves the key log collection ability, safe storage ability, tamper-proof material source ability.
Authentic Tamper-Proofing
Verifies the authenticity of the log uploaded by the broker and uploads the actual-time verification information to the block chain to ensure the authenticity of the uploaded log content and effectively eliminate the risk of log tampering.
Analysis & Supervision
For the logs after industry collection, big data analysis can be carried out on the log contents relatively independently to conduct regulatory analysis on the possible trading risks.
Solution
Provides a complete, unified, efficient, and accurate log audit platform solution for the industry supervision, according to the unified requirements of log query.
Problems & Demands
-
 Tightening Regulatory requirements
Tightening Regulatory requirements
-
 Difficult Data Sharing
Difficult Data Sharing
-
 Cumbersome and Inefficient Process
Cumbersome and Inefficient Process
-
 Diversified cyber attacks
Diversified cyber attacks
Technical Solutions
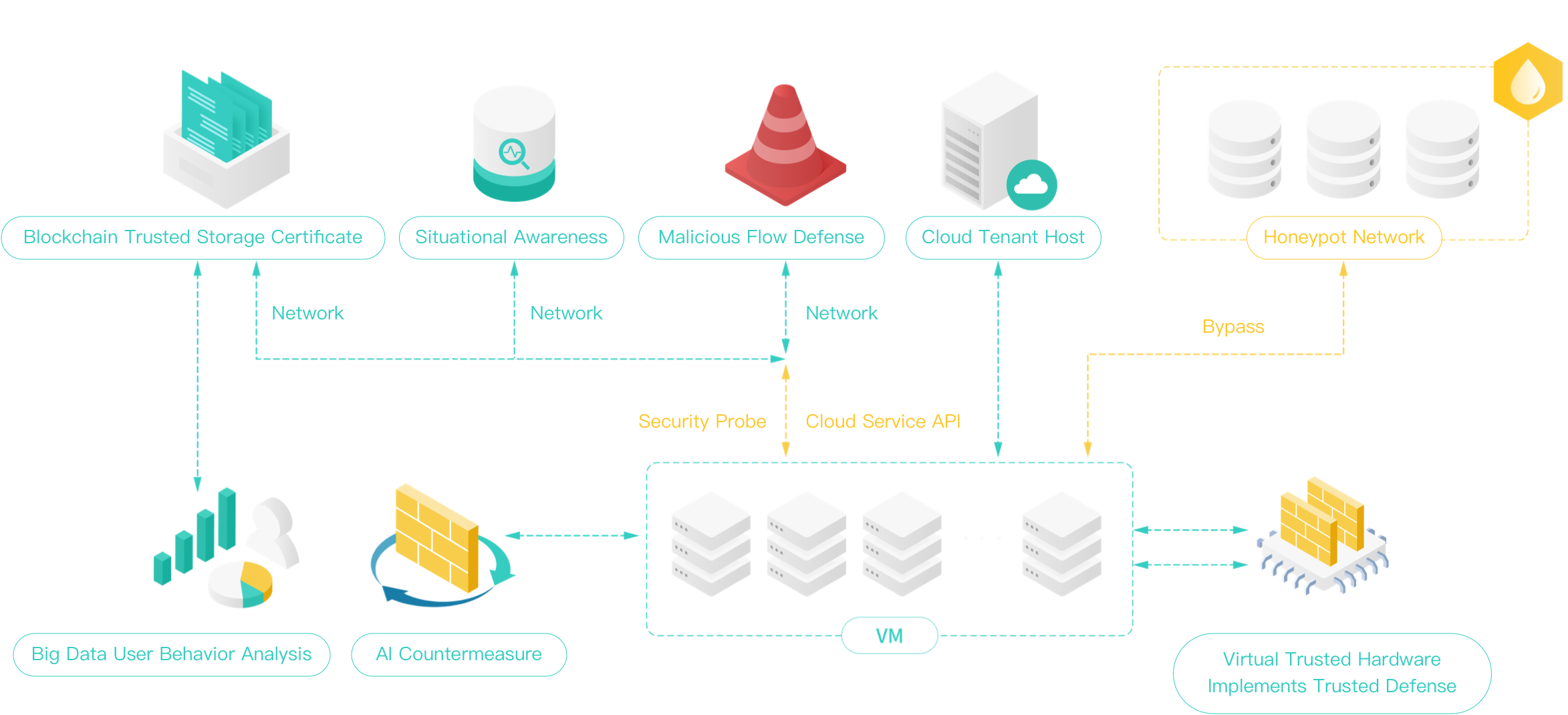
01.
Trusted Defense
Automatically generates the whitelist of the process conforming to the specification, and stores in the blockchain to improve the system security defense level, based on the continuous monitoring of the system by the trusted root verification service.
02.
Behavior Analysis
Collects system process, operation log and other multiple data sources, aggregates and analyzes user and system entity behavior, establishes behavior portrait, and effectively identifies abnormal behavior of user and entity.
03.
Storage Certificate Traceability
With the help of the tamper-proof property of blockchain, it can be applied in the fields of judicial deposit, copyright protection, anti-counterfeiting traceability and other fields under the government affairs scene to supervise all parties to restrain their own behavior.
Lower the Cost
The intelligentization of government affairs is improved, and the labor cost of security work is effectively reduced.
High Degree of Compliance
The information system has a high degree of compliance and meets the requirements of a series of laws and regulations such as cloud security and security of government affairs.
Complete Traceability
The business process is completely traceable to facilitate supervision and accountability.
Problems & Demands
-
 Large Proportion of Sensitive Data
Large Proportion of Sensitive Data
-
 Abuse of Power by Managers
Abuse of Power by Managers
-
 Inadequate Protective Measures
Inadequate Protective Measures
-
 Illegal operations are difficult to trace
Illegal operations are difficult to trace
Technical Solutions

01.
Authentication Mechanism
Provides multiple identity authentication mechanism, meets the requirements of equal protection, effectively prevents illegal user intrusion
02.
Communication Mechanism
Encrypts the whole process of data communication and circulation to ensure communication security and prevent information from being monitored or stolen.
03.
Protection Mechanism
Automatically generates the trusted whitelist, enables the protection, and monitors the trustworthiness status of the host on real-time.
04.
Alarm System
If abnormal or threat is found, alarms by various ways and notifies management personnel to deal with in time.
Behavior Supervision
Standardizes the operation behavior of intranet personnel with strict login authentication, combined with user behavior analysis technology, to achieve strict control of user behavior.
Permanent Storage with Certificates
Permanent storage of important data and logs with certificates to prevent malicious behavior such as data tampering.
Autonomous Countermeasure
When a threat occurs, intelligent protection can be activated to carry out autonomous countermeasures to ensure the security of network information.
医疗
当前医疗行业中,医疗数据孤岛导致医疗健康数据难以得到高效共享利用,医疗数据中心化的存储数据安全难以保障,个人医疗数据缺乏知情权及访问控制权,并且追溯困难;个人健康管理需求与健康数据有效管理矛盾
技术方案
01.
去中心化管理
去中心化的生产流水线,数据可信上链+流程溯源+供应链金融+可信交易合约
02.
协同办公平台
去中心化的可信大数据平台,无数据交换的多方数据协同处理,使医院数据不外流,运行结果在链上共享,并为所提供的算力和数据资源,从链上获得一定收益
03.
可信算力网络
去中心化的人工智能可信算力网络,无数据共享的边缘计算平台
专属数据
使用区块链技术,建立专属个人医疗数据账户,便于溯源,也可以减少二次医疗成本
数据共享
在系统设置授权提取下,医疗机构可以获取特定筛选条件下具体数据,但不包含具体的个人身份信息。既解决了医疗领域的数据孤岛难题又隐私
数据安全
建立的区块链账本,不论是公有链或者联盟链,其去中心化的特点可以完美解决医疗数据的安全问题,并且实现个人隐私的有效保护
Demands 教育
当前国家在职业教育领域加大力度,在原有补贴基础上新增注入千亿资金,促进职教改革、产教融合沿着标准化、产业化和国际化的大方向转型,同时也期许职教院校能够具备以独立姿态参加未来产业链市场化细分、重组的能力。
技术方案
01.
学分银行
构建学分银行用于就业资质、社会培训、岗前培训等的"学分-积分"互换机制
02.
课程共享
以学生和培训学员的学习和发展为中心,连通课程、教材的信息化和数字化开发,有助于支持开放课程、推进课程体系改革。
03.
数字教材
注重基于融合创新的课程教材数字化一体化建设,通过学分银行的主线贯穿在线教学、测评、作业、辅导和考试等若干环节,并为日常教学提供信息化平台的环境支撑。
04.
数字教学
为产教融合、校企合作协同开发在线课堂提供系统环境,为提高教师运用信息技术开展教学的能力和水平创造条件。
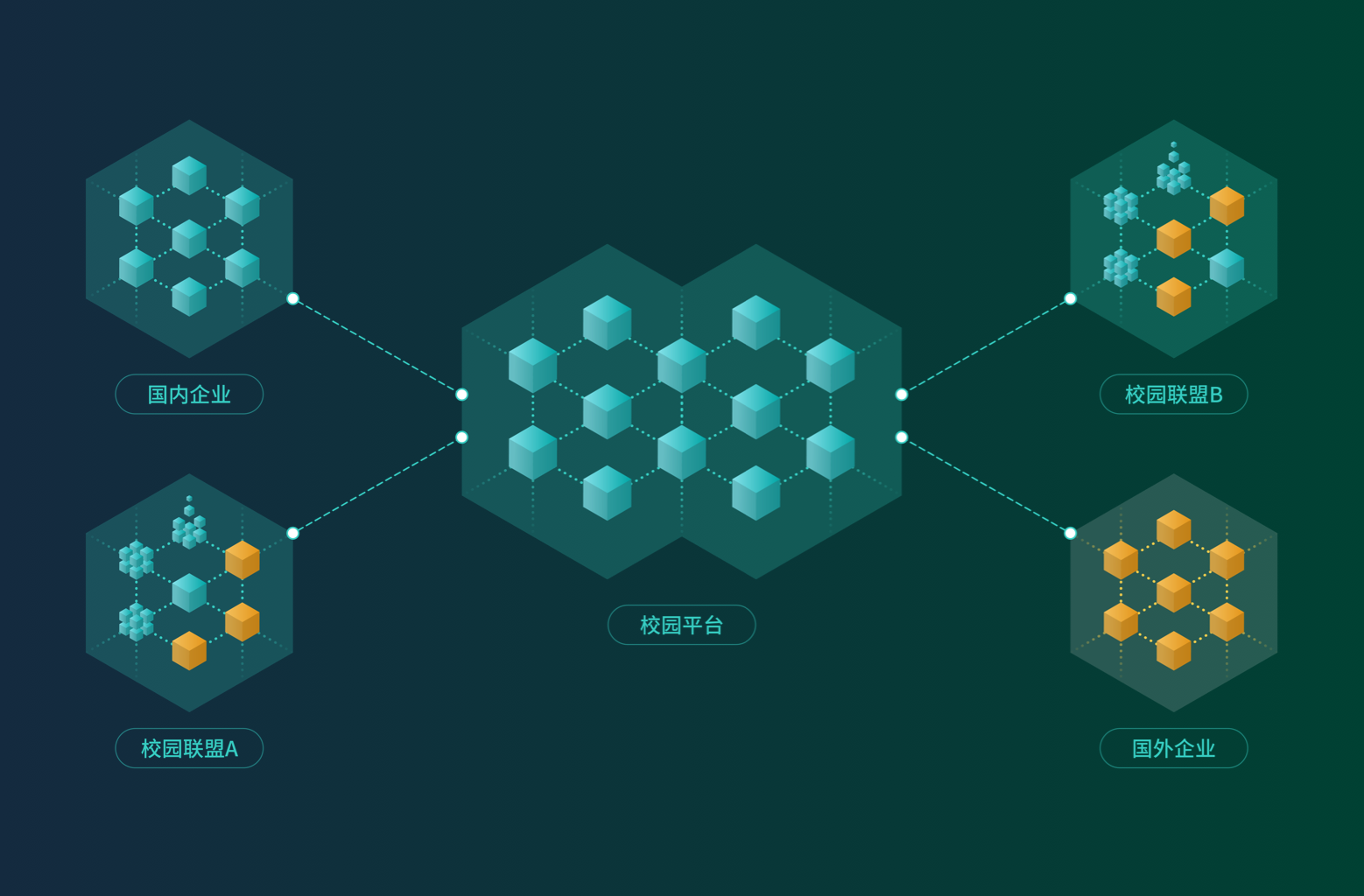
区块链核心
可以为构建校园、联盟、社会三层共享机制,使课程及其相关内容能够进行直接共享和交易,节省高昂成本
课程共享
联盟内学校之间能够共享课程,相互支付费用,并对课程和学分标准提供“众包式”的修订,并在联盟采纳后奖励建议老师相应的“学分”
学分应用
可以实现不同应用和换取其他在线服务;社会的员工可线参与课程学习,赚取学分,作为提高职业能力的证明。